Cyber Security Research Team and their very first achievements for the security community
As a team of R&D Unit, the Cyber Security Research Team understand the importance of focusing on research activities. The team itself has also set many ambitious goals in creating its image in the security community. And recently, some security vulnerabilities discovered by the team, have been officially recognized
About Cyber Security Research Team

Cyber Security Research Team is a division of R&D Unit, founded in April 2019 by Mr. Nguyen Anh Tien. Currently, after about 1 year of development, the team has 10 members including both employees and interns. The primary task of the Cyber Security Research Team is to ensure information security for the company's products as well as for its customers.
In addition to the main task as doing project tasks, the team also pays attention to research security vulnerabilities, participate in bug bounty programs, or contribute to the community, especially search for CVE.
What is CVE?

CVE stands for Common Vulnerabilities and Exposures. CVE was launched in 1999 by MITRE (a non-profit organization based in Bedford, Massachusetts, and McLean, Virginia, USA, which manages federally funded research and development centers, at the same time support a number of government agencies).
The purpose of this program is to classify and identify hardware or software vulnerabilities, gathered into an open system to standardize the process of authentication of known vulnerabilities. These vulnerabilities can lead to cybersecurity attacks in the form of hijacking the target system, hacking important user data such as address, phone number, bank card code. CVE is a database of security vulnerabilities, making it easier to share data across separate network security databases and tools.
A CVE listing only contains the standard identifier number with status indicator, a brief description and references to related vulnerability reports and advisories. By using the CVE ID for a particular vulnerability or exposure, organizations can quickly and accurately obtain information from a variety of CVE-Compatible information sources. Each vulnerability has its own unique identifier. For example, CVE-2020-12706 is a vulnerability discovered and published in 2020 with ID 12706.
These vulnerabilities will be published and updated daily on https://cve.mitre.org/.CVE can be considered as the contribution of teams and individuals who study security vulnerabilities for the community, make products safer as well as increase users’ awareness of security risks, help reduce attack risk when users make regular software updates.
Therefore, right from the very first days of its establishment, the Cyber Security Research Team has set orientations for finding CVE to contribute to the community later. This can also be considered as a way to help the team build its image and reputation in the domestic and international security community.
From orientation to setting realistic goals
Over a long period of building team, training members, finally, by the second quarter of 2020, Cyber Security Research Team realized that it was strong enough to set realistic goals for itself, related to CVE.
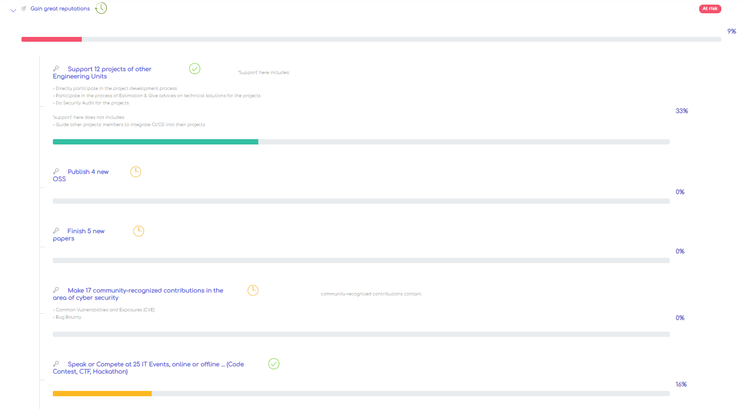
After a discussion about setting Unit's OKRs in the second quarter of 2020, the Group Leader and Team Leaders of the R&D Team officially set a Key Result: "Make 17 community-recognized contributions (including CVE & bug bounty) in the area of cyber security” for the objective "Gain great reputations". This demonstrates the importance of having research results recognized by the world-renowned organization and the expectations placed on the Cyber Security Research Team.
By setting OKRs to find CVE, it motivates the team members to work as well as encourages the desire to express themselves. Most of the team members are very young, and they haven't had experience in finding CVE. At the same time, the very ambitious goal which is to find nearly 20 CVEs in a quarter can be considered a big challenge for all members. At first, everyone was eager and enthusiastic, but after the first month they could not find any CVE, many members find it difficult to accomplish the goal the Unit has set.
But everyone doesn’t get frustrated by that, they all encourage each other in every daily team meeting and then together find out the way. After making a plan focusing on specific and important goals, the team has divided and set targets as some popular software.
The very first achievements
After addressing the problem, the team focuses on finding and exploiting common vulnerabilities on CMS Content Management platforms. Every time finding the bug, the members all share way and experience to find the points of doubt together, so that the vulnerability can be exploited. Sometimes the team finds bugs, but when they submit it to the Vendor (the product development unit that they are analyzing) or CVE, there is no response. So they have to stay at the company until the evening to simulate the bugs together, or they have to worry every day when CVE hasn’t been accepted.
However, after the relentless efforts, Team has achieved its first results, which some CVE are published on https://cve.mitre.org/. Last May 8 marked an important milestone, Cyber Security Research Team officially released the first exploit codes, which are widely recognized and published. CVEs found by the Team are vulnerabilities on CMS Content Management platforms such as php-fusion, uliCMS, leptonCMS, orchardcore, and most of them are related to XSS (Cross-site scripting) errors.
Here is a list of published CVEs:
- https://nvd.nist.gov/vuln/detail/CVE-2020-12703
- https://nvd.nist.gov/vuln/detail/CVE-2020-12704
- https://nvd.nist.gov/vuln/detail/CVE-2020-12705
- https://nvd.nist.gov/vuln/detail/CVE-2020-12706
- https://nvd.nist.gov/vuln/detail/CVE-2020-12707
- https://nvd.nist.gov/vuln/detail/CVE-2020-12708
In addition, CVEs with the codes CVE-2020-12709, CVE-2020-12710, CVE-2020-12711 have been recorded, but because the Vendor unit has not completed fixing the error and releasing the patch, the content of CVE have not yet public.
Some units have thanked the Cyber Security Research Team on the announcement about their vulnerability updates at https://en.ulicms.de/aktuelles.html?single=stored-xss-security-flaw-in-pagecontroller-fixed or at https://lepton-cms.org/posts/important-security-update-141.php
Because the goal of finding CVE has just been seriously planned by the team recently, and it has only been included in the R&D Unit's OKRs this quarter, the team decide to start from simple things first. The unit’s OKRs this time is also about the quantity, not the quality. Cyber Security Research Team knows that the CVEs that the team found this time didn’t have any serious or big impact; however, it is also a marker for a good start on the new journey to conquer challenges in security globally. Hopefully, in the future, the team will find more and more new CVEs, especially high rate ones (big impact, serious), or highly appreciated from the community.
“The journey of a thousand miles begins with a single step”

 VI
VI EN
EN